ThinkGeo Cloud
ThinkGeo UI Controls
ThinkGeo Open Source
Help and Support
External Resources
ThinkGeo Cloud
ThinkGeo UI Controls
ThinkGeo Open Source
Help and Support
External Resources
ThinkGeo Cloud offers a cloud-hosted suite of APIs that allow you to easily consume map tiles, geocode and reverse geocode, perform spatial operations and other GIS services. Whether you're just evaluating the Thinkgeo Cloud or you're a subscriber, this quick start guide will help you start consuming these services in your own applications.
You can login to the ThinkGeo Cloud with your ThinkGeo account, the same one you can use to access our community forums. If you don't have a ThinkGeo account yet, sign up for one here.
Then, visit the ThinkGeo Cloud web console login page at https://cloud.thinkgeo.com/login.html and click the “Login with ThinkGeo Account” button.
Once logged in, you'll be at the Dashboard page of the ThinkGeo Cloud web console. The Dashboard offers a quick look at the activity of your ThinkGeo Cloud clients over the past 24 hours. If you're a new user, you won't see any activity here.
You’ll want to start your experience by creating a *client* within ThinkGeo Cloud. A client is how you can enable your application or website to use ThinkGeo Cloud resources on your behalf. There are two types of clients for different kinds of applications, and each has its own ID and secret key. You can have as many clients in your account as you like.
To manage your clients, begin by clicking on the “Clients” button on the menu bar.
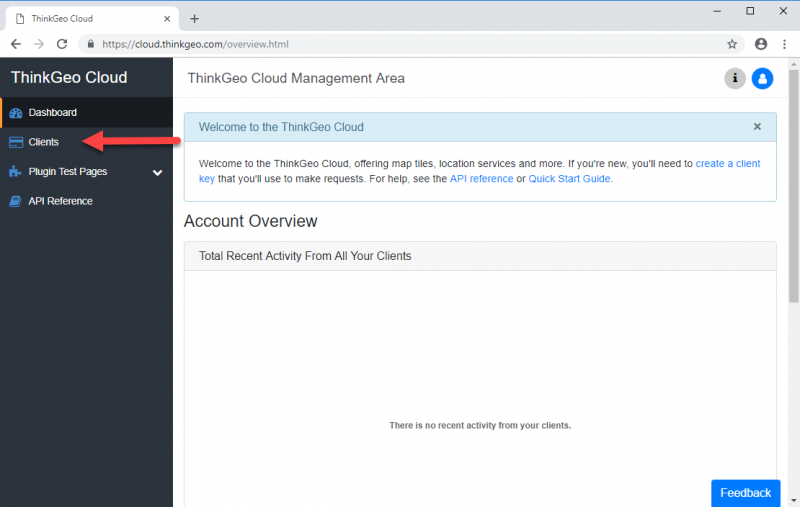
New ThinkGeo Cloud accounts come with two clients, one of each type, that you can use to quickly get started.
For now, let's use one of the default clients that come with your ThinkGeo Cloud account. For this exercise, we'll choose the Native Confidential client called “Sample Native Client”.
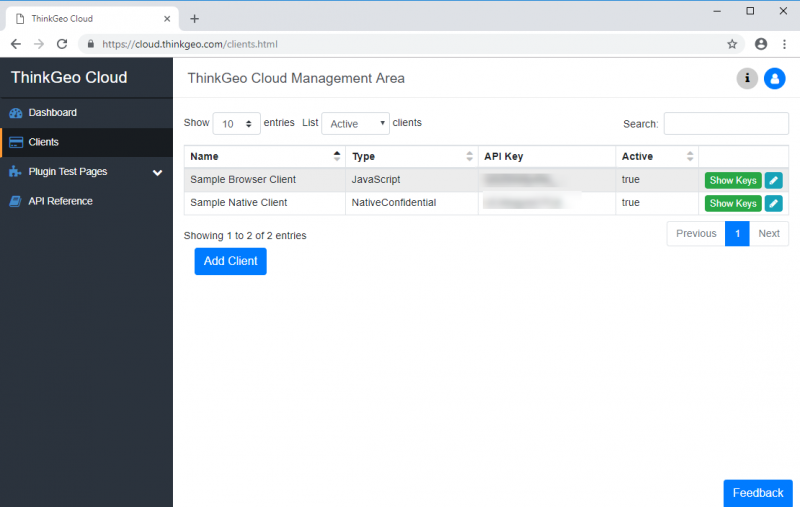
To use this client, you'll need its ID (or API Key) and secret. These can be displayed if you click on the green Show Keys button. The “Client Details” dialog will appear, showing you both the API Key and API Secret as follows:
You can use the “Copy” button to copy these values to your clipboard and use them in your application when authenticating.
Note: JavaScript clients will only have an API Key, since they are intended for use in browser-based applications where a secret cannot be kept secure.
You should take all necessary precautions to keep safe the API Key and API Secret – particularly the latter – of your NativeConfidential clients. Since these two values together can always be used to request an access token, if unauthorized users gain access to both of them, they can use your client in their own applications and the API usage will count against your ThinkGeo Cloud account.
For maximum security, if you are developing a client application that will be distributed to end users, it's a good idea to create your own web service or serverless function such as AWS Lambda to store your client key and secret. This service or function can then field requests from your application, call out to the ThinkGeo Cloud to get an access token, and then return it to application. Your application can then use the access token to make ThinkGeo Cloud API calls.
In contrast, JavaScript client API keys are less confidential, but you should take care to restrict them in the ThinkGeo Cloud web console so they can only be used from authorized sites or IP addresses.
The ThinkGeo Cloud web console lets you configure your clients so they can only be used from approved locations. This is a highly recommended step to ensure that only you are able to use your client keys.
On the “Clients” page of the ThinkGeo Cloud web console, pick the client you wish to secure and click the blue Pencil button. The “Edit Client” dialog will appear. Near the bottom, you'll see a text box where you can add restrictions for your client.
JavaScript clients can whitelist usage by Origin Domain (e.g. mywebsite.com) or IP Address/IP Range (e.g. 203.0.113.78). NativeConfidential clients can use IP Address/IP Range restriction only.
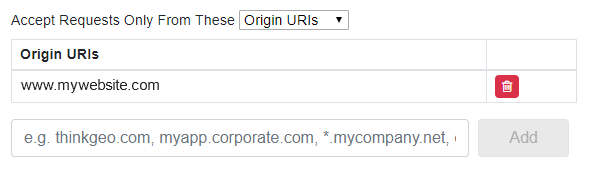
JavaScript clients can whitelist individual origin URIs (e.g. mywebsite.com) that are allowed to use the client. This is useful for web applications that are hosted on a particular domain, where no other web address should be allowed to use your client. You can enter:
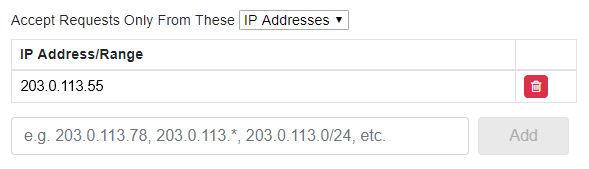
JavaScript and NativeConfidential clients can whitelist individual IP addresses or IP address ranges that are allowed to use the client. You can enter: